Debunking Custom DNS as a VPN replacement
https://x.com/levelsio/status/1923486824258994545
Ermm actually ... ☝🏻🤓
Ok, I get that @levelsio probably tweeted this on his phone while boarding his flight. But it's an oversimplification, and it has 2.9M views. If you're going to make a recommendation, you should get the details right.
It helps to have an architecture diagram as our foundation, our shared mental model.
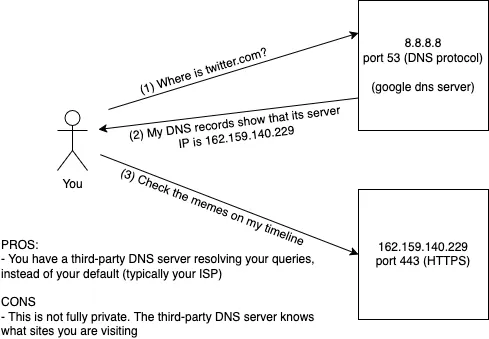
Claim 1: "HTTPS + set custom DNS to 8.8.8.8 or 1.1.1.1 and your traffic is always private"
"Always private"? How?
HTTPS provides encryption for your web traffic, but custom DNS only changes which provider sees your DNS queries. Instead of your ISP or default DNS provider, you're now sharing your browsing patterns with Google (8.8.8.8) or Cloudflare (1.1.1.1). This isn't privacy - it's just shifting who has access to your DNS query data.
Additionally, since this isn't DNS over HTTPS, your DNS queries remain in plaintext, visible to anyone monitoring your network traffic.
Claim 2: "The sites you visit are then sent to Google or Cloudflare and HTTPS encrypts the traffic end-to-end"
Ok wait now I'm beginning to think this guy doesn't know the difference between protocols. That, or this sentence is worded deceivingly.
When you use Google (8.8.8.8) or Cloudflare (1.1.1.1) DNS servers, they log your IP address and the domains you query. This creates a record of your browsing patterns.
The actual connection to websites happens in two distinct steps:
- DNS resolution: Your device queries the DNS server to get the website's IP address
- HTTPS connection: Your device establishes an encrypted connection directly with the website's server
While HTTPS encrypts the content of your communication, it doesn't hide:
- Your IP address
- The website's IP address
- Your DNS queries
- The fact that you're connecting to specific servers
Calling this "end-to-end encryption" is misleading. True end-to-end encryption would protect all aspects of the communication, not just the content.
What the recommendation should've been
Always use HTTPS - it's essential for secure web browsing.
Custom DNS can be a limited privacy tool, but it's not a security solution. It simply changes who sees your DNS queries, not whether they're visible.
For comprehensive privacy and security:
- Use HTTPS for encrypted connections
- Consider DNS over HTTPS to encrypt DNS queries
- Use a VPN to mask your IP and encrypt all traffic
- Layer these tools together for better protection